THE BYOD SMARTPHONESECURITY PROTECTION SOLUTION FOR TELCO, ENTERPRISE AND GOVERNMENT
Networks presents the only all-in-one
ANTI-TAPPING / ANTI-HACKING / THREAT MANAGEMENT
solution for comprehensive protection of BYOD smartphones.
Networks’ solution provides protection to:
ENTERPRISE, GOVERNMENT and the TELECOMMUNICATIONS INDUSTRY.
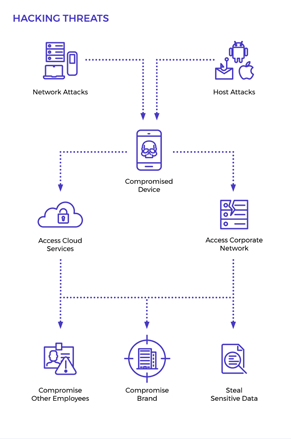
Smartphones are exposed to constant cyber threats.
Tapping
Eavesdropping—either at the access network or the switch.
Hacking
Data theft, malicious software or use of the device as a backdoor into the corporate network
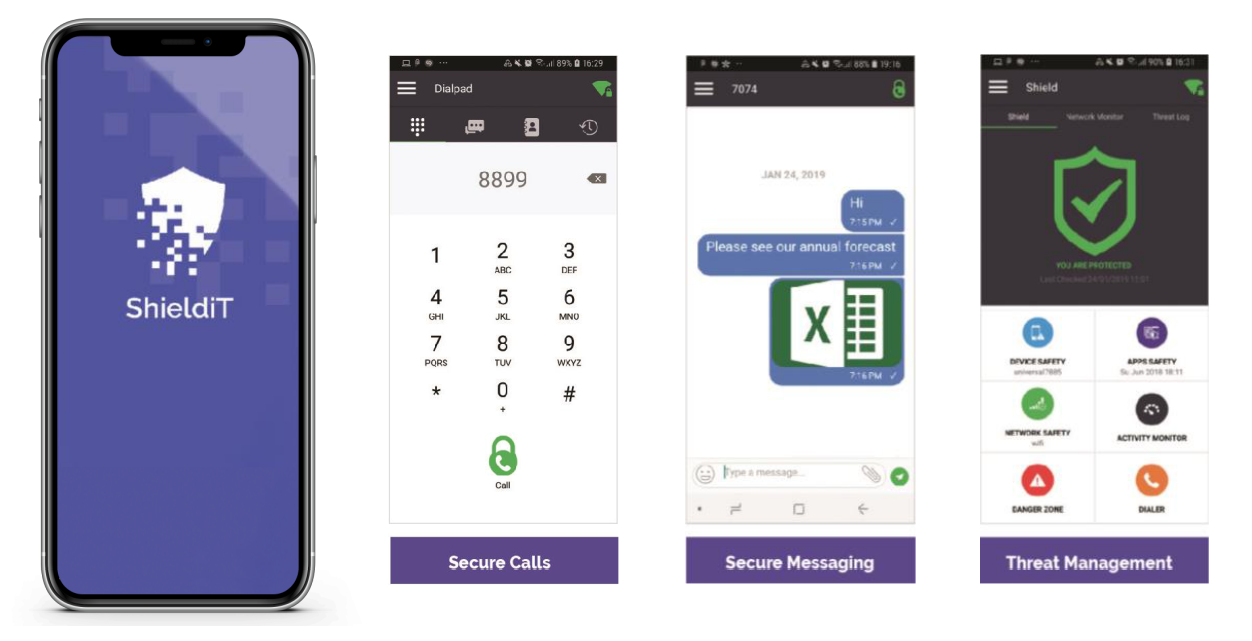
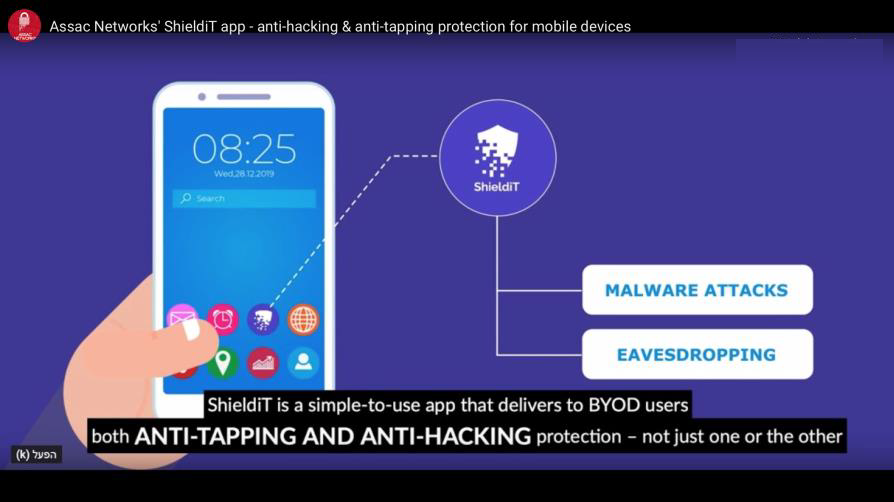
The only anti-hacking, anti-tapping& threat management protection for Bring-Your-Own-Device smartphones.
Anti-tapping
Point-to-any-point, military-grade voice and text message encryption and eavesdropping prevention.
Anti-hacking
Cyber-attack, data theft and malware detection and prevention
Threat Management
Robust, AI-powered threat management with a user-friendly dashboard
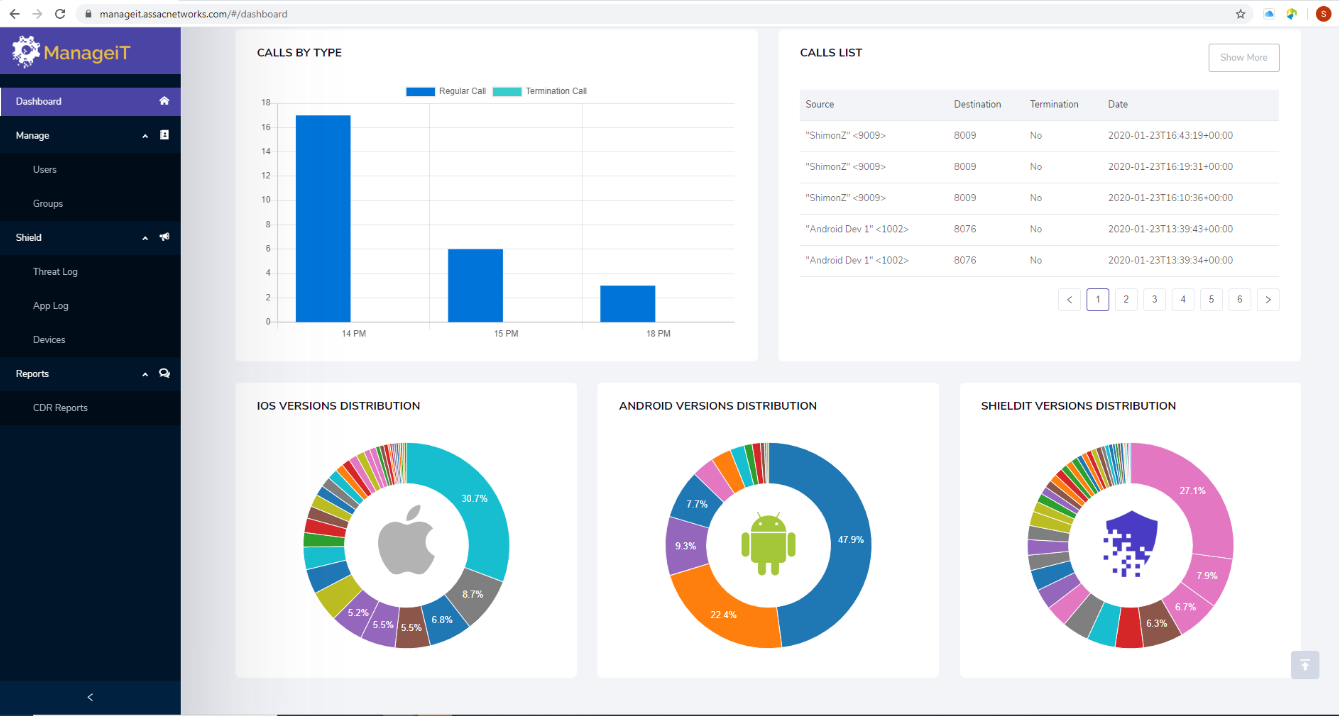
An intuitive, easy-to-use managementdashboard that centrally controls allShieldiT features
v Complements ShieldiT
v Allows CISOs to control and monitor the security of smartphones
v Control access to the premium “international calls” feature
v Manage encryption keys
v The synergy of ManageiT & ShieldiT affords corporations the ability to control and conduct incident response from the management console.
“Assac Networks offers a secured smartphone solution for a fraction of the cost of an encrypted phone which sells for thousands of dollars per device. ShieldiT is the leading secure and affordable smartphone protection for enterprise users.”
v Unified managed Anti-hacking and Anti-tapping solution for BYOD Smartphones
v Fully controlled Encryption with autonomous CA
v High Level Cyber Protection
v Easy and rapid smooth Integration with corporates network
v Affordable, best price performance
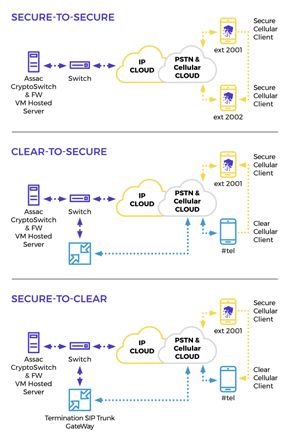
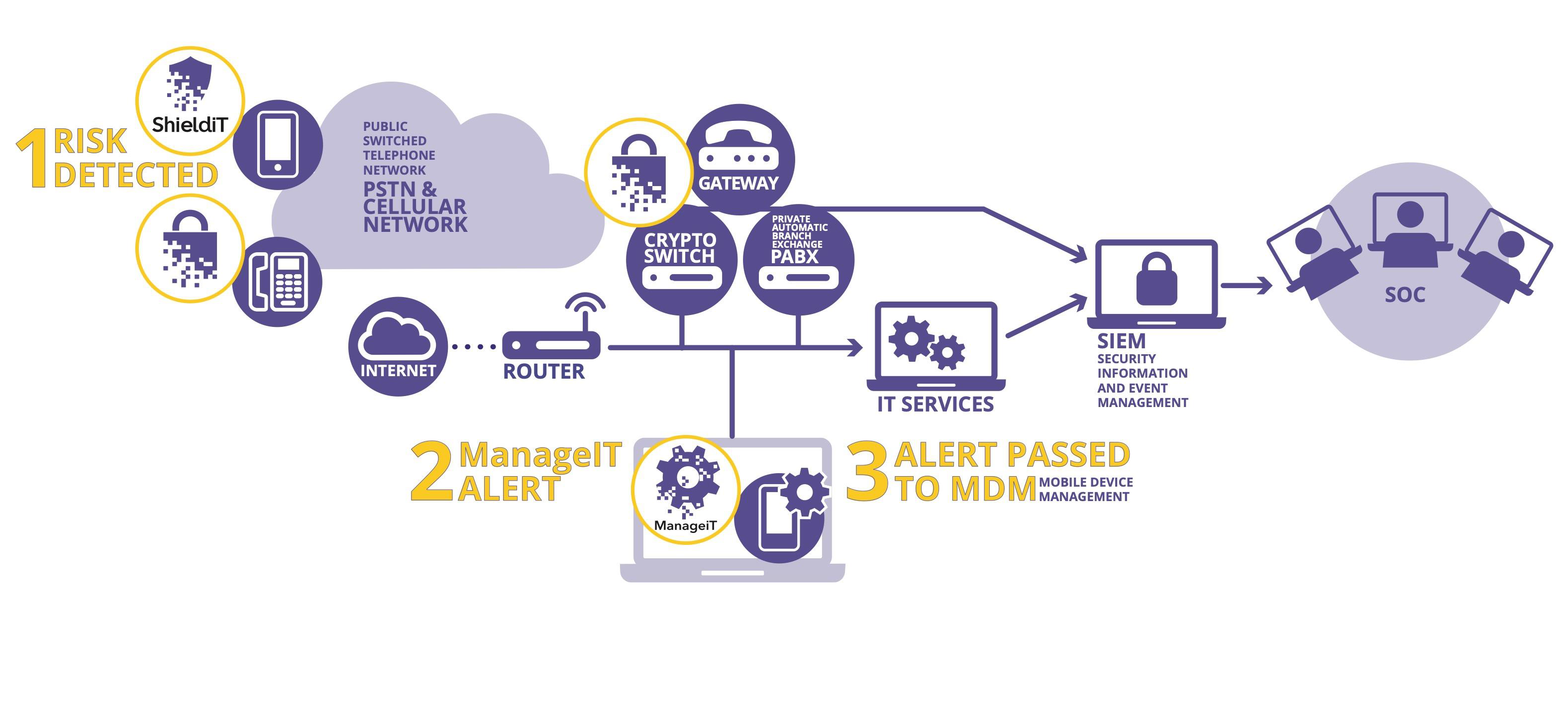
ShieldiT and ManageiT are easily integrated into existing ITinfrastructures
v Voice networks (PBX): integration via the Assac Gateway
v Computer networks: integration via the SIEM (QRadar) and MDM policy enforcement (IBM)
Four major telecommunications companies POCs with Telefonica & Telkomsel
Business Model
v Fixed Price or Revenue Share (following a POC)
Subscription Period
v Minimum one year
Services Offered
v Complete cloud-based combined license w/ SDK for operators
v Virtual machine running on operator’s network
v Bulk end-user license for ShieldiT app
v Manager’s license for ManageiT console included
v Full OEM
v Integration with telco switch for PSTN calls
Enterprise Benefits
Business Model
v SaaS (Software as a Service)
Subscription Period
v One or three years
Services Offered
v End-user license for ShieldiT app
v Manager’s license for ManageiT console

Keeping Sensitive Government Communications Confidential
Business Model
v Leveraging long-term relationships and reputation of Assac Networks, sold through defense system integrators
Contract Duration
v Three years
Services Offered
v On-premise or cloud deployment
v End-user license for ShieldiT app
v Manager’s license for ManageiT console
v Professional services (CA, OEM, additional equipment, etc.)
